
Bid farewell to skimming over endless reviews and ...
news-extra-space

 The actors who were threatening the victim claimed to be looking to hire the employee to work at Amazon. They sent the target a message over WhatsApp that transmitted a file named amazon_assessment.iso. ISO files are increasingly employed in recent times to cause damage to Windows computers due to the fact that the double-click on them triggers them to be mounted as an virtual machine. In addition the image was an executable file named PuTTY.exe.
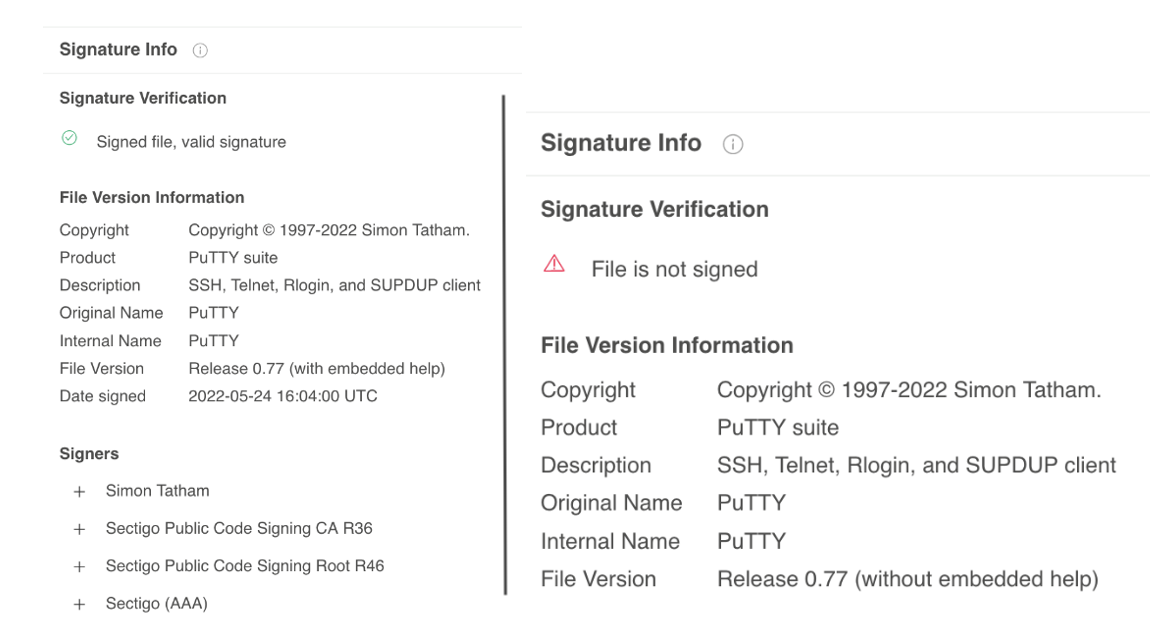
PuTTY is an open-source secure shell application and telnet. The secure versions are authenticated by the official developer. The version that was sent in the WhatsApp message was not signed by the official developer.
The executable files installed the most recent version of Airdry an attack on the backdoor which the US government has blamed on it being the North Korean government. It is reported that the US Cybersecurity and Infrastructure Security Agency has a description of the backdoor here. Japan's emergency response community provides an explanation of the backdoor which is tracked under BLINDINGCAN.
The actors who were threatening the victim claimed to be looking to hire the employee to work at Amazon. They sent the target a message over WhatsApp that transmitted a file named amazon_assessment.iso. ISO files are increasingly employed in recent times to cause damage to Windows computers due to the fact that the double-click on them triggers them to be mounted as an virtual machine. In addition the image was an executable file named PuTTY.exe.
PuTTY is an open-source secure shell application and telnet. The secure versions are authenticated by the official developer. The version that was sent in the WhatsApp message was not signed by the official developer.
The executable files installed the most recent version of Airdry an attack on the backdoor which the US government has blamed on it being the North Korean government. It is reported that the US Cybersecurity and Infrastructure Security Agency has a description of the backdoor here. Japan's emergency response community provides an explanation of the backdoor which is tracked under BLINDINGCAN.
Leave a Reply






